

Power Management: Lets you configure power management options for the device. When you click OK to dismiss the dialog box, the network connection’s Properties dialog box closes and you’re returned to the Network Connections page. Right-click the network adapter and choose Properties again to continue the procedure.
Today, I will be going over Control 11 from version 7 of the top 20 CIS Controls – Secure Configuration for Network Devices, such as Firewalls, Routers, and Switches. I will go through the seven requirements and offer my thoughts on what I’ve found.
Description: Maintain standard, documented security configuration standards for all authorized network devices.
Notes: As with control number 5, network devices also are candidates to be hardened. Both CIS and DISA have guidelines available to harden these types of devices. A tool such as Tripwire Enterprise will make this much easier.
Description: All configuration rules that allow traffic to flow through network devices should be documented in a configuration management system with a specific business reason for each rule, a specific individual’s name responsible for that business need, and an expected duration of the need.
Notes: Getting the rules documented is the easy part. Tying assets and applications on those assets back to an individual or business unit is the hard part, especially for businesses which are organic. The first step is to gather the configuration and leverage the next section to alert on changes.
Description: Compare all network device configurations against approved security configurations defined for each network device in use and alert when any deviations are discovered.
Antivirus zap virus & adware 3 0 1. Notes: Monitoring for change just isn’t for endpoints. Attackers can modify network device configurations to destabilize a network or allow connections in/out of the environment. A tool like Tripwire Enterprise can identify changes and report the proper administrator very quickly.
Description: Install the latest stable version of any security-related updates on all network devices.
Notes: It doesn’t matter how secure your endpoints are if the firewall is using firmware from five years ago. You may be surprised at how often updates are available for these devices if you aren’t actively looking for them. By using outdated firmware, you could be leaving the front door wide open to the entire world.
Description: Manage all network devices using multi-factor authentication and encrypted sessions.
Notes: There are two parts to this requirement which I feel should be split out. The first is using encrypted communications to manage the devices. For example, use SSH instead of Telnet or HTTPS over HTTP. The benefits of that are well known by now. However, requiring MFA for network devices may not be supported. Even if they are, it may be overkill for the internal network. If you are doing remote administration over the internet, however, then MFA should be implemented ASAP.
Description: Ensure network engineers use a dedicated machine for all administrative tasks or tasks requiring elevated access. This machine shall be segmented from the organization’s primary network and not be allowed Internet access. This machine shall not be used for reading email, composing documents, or surfing the Internet.
Notes: The authors of this document are obviously worried about common attacks such as phishing, which could infect an administrator’s workstation with credential stealing malware. This is one of those requirements that is going to cause additional overhead for folks but is necessary for a more mature organization. If there are password management or network device management tools which are accessed, they should be included in this requirement, as well.
Description Manage the network infrastructure across network connections that are separated from the business use of that network, relying on separate VLANs or, even more preferable, entirely different physical connectivity for management sessions for network devices.
Notes: For the same reasons as was stated in the previous requirement, a dedicated network will reduce the chances of credential stealing malware from gaining a larger foothold on the network.
See how simple and effective security controls can create a framework that helps you protect your organization and data from known cyber attack vectors by downloading this guide here. Iphoto library manager 4 2 4 download free.
Control 20 – Penetration Tests and Red Team Exercises
Control 19 – Incident Response and Management
Control 18 – Application Software Security
Control 17 – Implement a Security Awareness and Training Program
Blender software download 64 bit. Control 16 – Account Monitoring and Control
Control 15 – Wireless Access Control
Control 14 – Controlled Access Based on the Need to Know
Rhinoceros 5 3 2 2017. Control 13 – Data Protection
Control 12 – Boundary Defense
Control 11 – Secure Configuration for Network Devices, such as Firewalls, Routers, and Switches
Control 10 – Data Recovery Capabilities
Control 9 – Limitation and Control of Network Ports, Protocols, and Services
Control 8 – Malware Defenses
Control 7 – Email and Web Browser Protections
Control 6 – Maintenance, Monitoring, and Analysis of Audit Logs
Control 5 – Secure Configurations for Hardware and Software on Mobile Devices, Laptops, Workstations, and Servers
Control 4 – Controlled Use of Administrative Privileges
Control 3 – Continuous Vulnerability Management
Control 2 – Inventory and Control of Software Assets
Apple service toolkit 1 0 7 download free. Control 1 – Inventory and Control of Hardware Assets
You can also learn more about the CIS controls here.
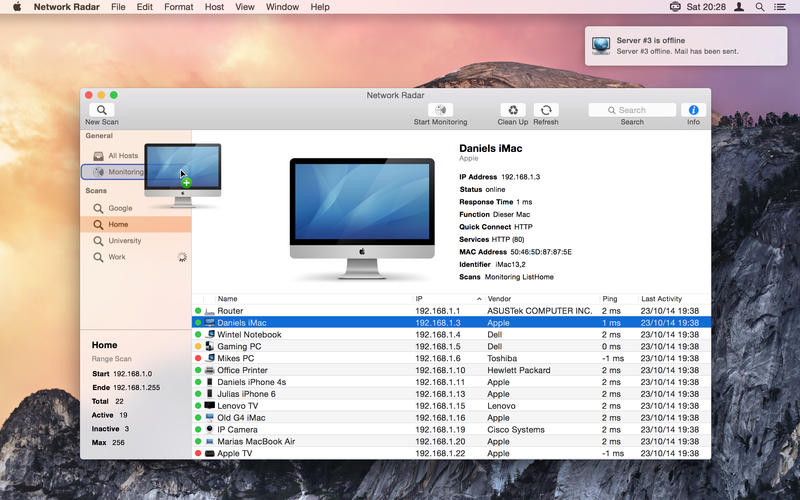
Download Network Radar 2.4 for Mac free latest version offline setup. Network Radar 2.4 for Mac is a reliable application for dealing with the management of the network and the internet.
A professional networking application, Network Radar 2.4 comes up with a wide range of powerful tools and options to monitor the network and provides useful information. It has a straightforward user interface with a variety of powerful options that enhance the overall workflow. Also, it is very easy for the novices to operate the application. It scans the internet and gets complete information about the connected devices.
Moreover, the application provides support for exporting the reposts as CSV and TXT formats and allows the users to run different commands. The application has the possibility to run different commands and receive notifications. All in all, it is a very powerful application to deal with the network and provide useful details about the devices on the network.

Click on the below link to download the latest offline setup of Network Radar 2.4 for Mac OS X. You can also download iNet Network Scanner 2.4.
